In the latest installment of our Privacy Protectors Spotlight series, we are excited to feature James Everett Lee, a leading figure in the fight against identity crime. James is a seasoned executive and subject matter expert in data security, privacy protection, and identity management. He currently serves as the Chief Operating Officer of the Identity Theft Resource Center (ITRC), the nation’s leading nonprofit organization dedicated to assisting victims of identity crimes and advising public policy and business leaders on issues related to privacy, data security, and identity.

In his role at ITRC, James is responsible for day-to-day operations and has spearheaded initiatives to expand the Center’s products and services, branding, messaging, and revenue. His leadership has driven the development of a data breach tracking and alert service, widely used by both consumers and government agencies, and has significantly increased the ITRC’s presence in media coverage of identity topics.
Before joining the ITRC as COO in 2020, James served for more than a decade on the organization’s Board of Directors, including three years as Chair. His deep understanding of consumer privacy and data security laws has made him a sought-after expert for media outlets and industry publications, where he regularly provides insights on how these issues impact marketing and business operations.
Since January 2009, James has been the Principal Consultant at James Everett Lee Strategies LLC, where he provides expert guidance on data protection, data security, identity management, and business identity theft. In this role, he helps executives and marketers turn around operations and restore reputations in the wake of controversies, as well as navigate the changes required by new state privacy laws.
James has also held prominent roles in the corporate world. He was Executive Vice President and Company Secretary at Waratek, an Irish cybersecurity company, and Senior Vice President and Chief Marketing Officer at ChoicePoint, a data broker company, now part of LexisNexis. In 2005, ChoicePoint became widely known after it sold data to identity thieves posing as legitimate businesses, compromising the personal information of over 163,000 individuals. As part of a reputation management program led by James, the company issued the first nationwide data breach notice in the United States. At that time, the only state with a legal requirement to notify individuals of data breaches was California. By leading the effort to issue a voluntary nationwide notice, ChoicePoint and James’ team set a precedent for transparency in data breaches. This action served as a catalyst for other states to adopt their own data breach notification laws.
James has also chaired working groups for the American National Standards Institute (ANSI) on identity management and privacy, contributing to the development of industry standards. He holds academic credentials from the University of Arkansas, the University of Pennsylvania’s Wharton School of Business, and the University of Texas School of Information’s Center for Identity. Beyond his professional achievements, he is an avid baseball fan and a collector of pop culture memorabilia, known for his love of trivia and “useless facts.”
James E. Lee and the Role of the ITRC
As COO of the Identity Theft Resource Center (ITRC), James E. Lee has provided invaluable expertise on the evolving nature of identity crimes. The ITRC plays a crucial role in not only assisting victims of identity theft but also educating consumers, businesses, government institutions, and academic entities, all of which benefit from the ITRC’s extensive research into the ever-changing landscape of identity crimes.
The ITRC has built the largest repository of publicly reported data breaches and identity compromises. Initially starting with a single notice and a few data points nearly 20 years ago, the repository has now expanded to include over 20,000 breaches, each detailed with up to 96 data points, and is continuously updated daily. This vast repository provides insights that support the ITRC’s efforts to educate and protect consumers, businesses, and government entities. As part of these efforts to educate the public, Lee himself has been instrumental in helping to convey the ITRC’s findings and concerns.
The ITRC’s Research and Insights
In an interview conducted in 2022 with Legal Talk Network, Lee highlighted a significant shift in the focus of identity criminals, starting in late 2018 and continuing up through today. This shift has involved moving from primarily targeting individuals to leveraging stolen personal data to attack businesses. This new trend marks a fundamental change in the way identity crimes are perpetrated. Lee explained:
“Now, the way they do that, more often than not, is they use the information of individuals—of individual consumers. So, that personal information is still very important to an identity criminal, but they’re not coming after your resources; they’re coming after the resources of a business using your information. That is fundamentally different than any other time since what we have historically thought of as a data breach. It is a fundamentally different time period, and the way these crimes are being committed reflects that—it’s changing and, in some cases, accelerating.”
In addition to highlighting this shift, Lee has also brought attention to the problem of ineffective breach notifications and the inadequate public responses to them. He noted:
“One of the things that we found, both in our research and in talking to people who have had data breaches, been affected by a breach, or received a breach notice, is that how people react to that notice is kind of discouraging. A lot of it comes down to both the form of the notice and the way it’s delivered. It doesn’t really help individuals know how to respond. They don’t really know what actions they need to take. They don’t really understand the threat that may exist because their information is now in the wild.”
To address this, the ITRC has developed tools that provide timely alerts to individuals whose data may be compromised, offering them guidance on protective measures they can take before their information is misused. In the interview, Lee elaborated:
“What we have done is we’ve created a mechanism where someone can come to the ITRC, visit our website, and enter the names of organizations that are important to them—like your bank, credit card company, or health provider. You create a list, and if at any point those organizations issue a public notice of a data breach, you’ll get an alert from us. We’ll tell you what happened, when it happened, and provide resources to help you prevent that information from being misused. Just because it’s been breached doesn’t mean it will be misused immediately—there’s usually a lag, sometimes years, sometimes soon, and sometimes never. But we want people to take preventive actions immediately so they don’t have to worry about their information being misused because it can be blocked.”
Lee emphasized the critical connection between data protection and cybersecurity, highlighting how modern threats often bypass traditional defenses through the exploitation of stolen personal information.
“Ransomware is a very serious issue, both from a cybersecurity perspective and a data protection perspective, because people are stealing individuals’ data to commit these ransomware attacks. They want logins and passwords. That’s what’s getting the threat actors into these organizations—they don’t have to break in using some sort of sophisticated cyberattack. They don’t need a hacking event, as most people think of when they hear ‘cyberattack’; they just walk right in because they’ve got a legitimate login and password that’s been stolen from an individual.”
Lee described the value that identity criminals place on personal data, especially administrative email login credentials:
“If you are the administrator of a business email system, your administrator password is worth hundreds of thousands of dollars to an identity criminal. That’s one of the things we have to sort of get our heads around is the world has changed and it’s not that we have to stop protecting the information we’ve been protecting for the last decade. It’s that we’ve got to start protecting other kinds of information with the same level of care.”
Lee noted that the tactics of identity criminals are now more focused on the quality rather than the quantity of stolen personal data, though he notes “they will find the way to use just about any data they can get their hands on”. As a result, cybersecurity defenders must recognize the full value of personal information in the hands of these criminals and adapt their protection strategies accordingly.
2021 Senate Testimony
In his testimony titled “Securing Americans’ Identities: The Future of Identity Protection,” delivered before the U.S. Senate Committee on Commerce, Science, and Transportation’s in 2021, James E. Lee provided an overview of the ITRC’s mission and the challenges posed by identity crimes.
The ITRC offers free assistance to victims of identity crimes through a contact center staffed by trauma-informed advisors and Lee stated that the center was helping approximately 11,000 victims annually, assisting them in recovering stolen identities and providing guidance to consumers on how to protect themselves from identity crimes. Additionally, he said the ITRC’s educational outreach extends to over a million people worldwide who hold U.S. identity credentials, including military personnel, helping them safeguard their personal information and stay informed about the latest scams.
Lee highlighted the ITRC’s role in maintaining the largest repository of publicly reported data breaches and leveraging this extensive data to produce annual and quarterly reports that analyze trends in identity crimes and data compromises. The ITRC also produces the Consumer Aftermath Report, the only comprehensive study on the total impact of identity crimes on consumers, and the Business Aftermath Report, which examines the effects of security and data breaches on small businesses and entrepreneurs.
Lee testified that the ITRC works closely with federal agencies, including the Federal Trade Commission (FTC), Internal Revenue Service (IRS), Department of Homeland Security (DHS), and state and local law enforcement, to provide specialized support for identity crime victims. These partnerships are critical in addressing complex identity theft cases that larger organizations are often not equipped to handle.
To illustrate the real-world impact of identity crimes, Lee provided an example of the dramatic rise in identity-related unemployment benefits fraud during the Covid era. He explained how cybercriminals exploited vulnerabilities in state unemployment systems, leading to widespread fraud that affected millions of Americans. The ITRC played a crucial role in assisting victims of this fraud, highlighting the importance of its work in responding to emerging threats.
Lee emphasized the need for better cybersecurity standards and practices, arguing that many cyberattacks are preventable with enforceable minimum standards. He criticized the current “cheaper to pay the fine” mentality prevalent among some organizations and advocated for stronger enforcement mechanisms to protect victims. Lee also called for a more effective victim notification system, suggesting that the U.S. could learn from the European Union’s General Data Protection Regulation (GDPR) in this regard. He stressed the importance of mandatory reporting with strong penalties for non-compliance and greater transparency in breach notifications.
Lee underscored the inadequacies of the current victim support system and expressed the ITRC’s commitment to working with policymakers to improve protections for identity crime victims. He urged a focus on three key areas: enhancing cybersecurity standards, improving enforcement mechanisms, and reforming the victim notification system, to better protect citizens and the homeland.
2024 Senate Testimony
In his May 8, 2024 testimony before the U.S. Senate Committee on Commerce, Science, and Transportation Subcommittee on Consumer Protection, Product Safety, and Data Security, James E. Lee discussed the alarming rise in identity crimes, dubbing this era the “Golden Age of Identity Crime.”
Referring to his previous testimony, Lee noted that the personal information stolen during Covid was, and still is, being “used to open bank accounts, obtain loans, and trick innocent, trusting people into willingly sharing personal information with someone they thought they knew – often on a social media platform or as part of a romance scam.” He also noted that the needs he discussed in his previous testimony to reduce the number of identity crime victims remained the same.
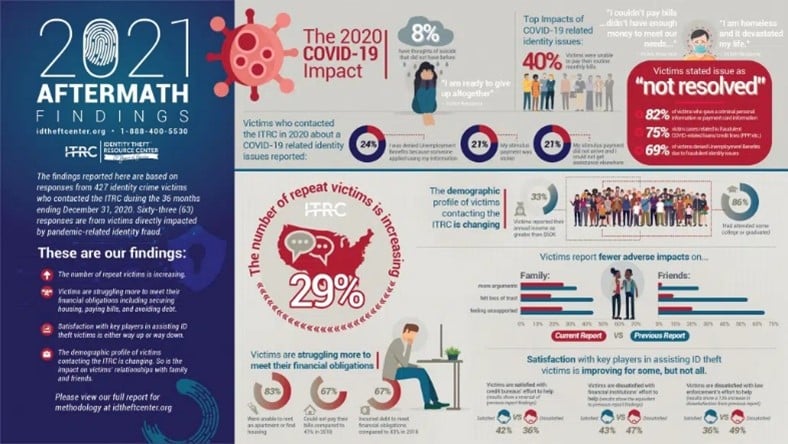
Lee testified that while the number of individual victims per breach has decreased, the frequency of identity misuse among those impacted has risen sharply. By 2023, 41% of those contacting the Identity Theft Resource Center (ITRC) had experienced multiple instances of identity misuse, a stark increase from 29% in 2021. Alarmingly, this figure reaches 69% among the general population who do not seek ITRC assistance.
Lee warned of the evolving tactics of cybercriminals, including their use of AI to exploit vulnerabilities and carry out sophisticated attacks. He emphasized that these more targeted breaches are now affecting a broader set of businesses, even as the overall victim count per attack has declined. For instance, while data breaches in Q1 2024 increased in 15 of 17 industries year-over-year, the total number of victims decreased, highlighting a shift towards more precise, goal-oriented cyberattacks.
In addressing the prevention of identity crimes, Lee called for minimum cybersecurity and data protection standards, regular risk assessments, and the enforcement of cybersecurity laws backed by audits. He also stressed again the need for a reform of the data breach notification system, which has become increasingly ineffective, particularly noting that many no longer include the root cause of the attack, leaving companies and individuals ill-prepared to prevent future breaches.
Lee highlighted the concept of data minimization, urging organizations to limit the collection and retention of personal information to reduce the risk of exposure. He stated: “Data minimization is predicated on a simple truth: you cannot lose control of information you don’t have or haven’t secured. The logic is not complicated. If you don’t need the information to complete a business transaction, don’t collect it. If you need it, delete it as soon as the transaction is completed unless you are required to keep it. If you must keep the information, make sure it is secure and encrypted.”
Furthermore, Lee advocated for the responsible use of biometric verification to devalue stolen personal information, thereby reducing the incentive for criminals to steal such data in the first place. He underscored the importance of fostering a company culture where security and data protection are integral to every team member’s role.
Conclusion
James Everett Lee’s leadership continues to drive essential conversations and advancements in the field of identity protection. His work at the ITRC not only supports countless identity crime victims but also shapes the broader strategies necessary to reduce the number of victims and mitigate the impact of identity fraud. Through the ITRC’s website and outreach programs, millions of individuals have learned how to protect their personal information from misuse.
At Optery, we are greatly inspired by James’s efforts and are happy to spotlight his outstanding contributions to privacy protection.
Join us in recognizing James E. Lee’s important work. To stay updated on his work and the ITRC’s invaluable resources, be sure to follow James E. Lee on LinkedIn and visit the ITRC’s website for the latest news and help on mitigating risk and minimizing impact of identity compromise.
Stay tuned for more features in our Privacy Protectors Spotlight series and follow Optery’s blog for further insights on safeguarding your personal information.
