Financial Services
- Remove Employee Personal Data.
- Reduce Cyber & Physical Risk.
- Protect Your People & Institution.

The Threat Landscape
Financial Services was the most breached industry in the first half of 2025 (ITRC H1 2025 DBR).
The top attack patterns were system intrusion and social engineering, often driven by phishing and stolen credentials (Verizon 2025 DBIR).
These attacks are fueled by exposed employee and executive data from data brokers and people search sites.

Threat actors use data broker & people search sites to:
- Target employees and executives with tailored lures
- Combine leaked credentials and PII to access accounts
- Launch fraud, impersonation, and ransomware attacks
Optery finds and removes this data more thoroughly than any other service, closing a major gap in financial sector security.
Prevent Financial Sector Threats
Prevent Social Engineering Attacks and Credential Compromise
Remove the exposed PII that fuels phishing, smishing, and BEC.
Safeguard Executives &
High-Risk Staff
Protect the employees attackers
most often target.
Lower
Alert Volumes
Cut down on incidents and decrease the burden on your security team.
Demonstrate
Risk Reduction
Show regulators, auditors, insurance carriers, and partners that you’re closing a major security gap.
Compliance & Regulatory
Alignment
Supports GLBA Safeguards Rule obligations to protect customer data by eliminating exposed employee PII that enables unauthorized access.
Helps meet NYDFS cybersecurity obligations by reducing employee and executive data exposure that can lead to compromise of nonpublic information.
Supports FFIEC CAT objectives around reducing inherent risk and strengthening controls against external threats like social engineering.
Why Financial Institutions
Choose Optery
Patented Search Technology
Finds significantly more data broker profiles per person — ~100 on average, including 40–50 missed by competitors.
Before-and-After Screenshot Proof
The only service that provides visual evidence of removals.
AI-Powered Automation
Harnesses advanced AI to streamline and accelerate complex data broker opt-out workflows with intelligence and precision. From verifying results to adapting to new sites and handling updates automatically, Optery’s AI operates securely and effectively.
Unmatched Coverage
Covers 640+ brokers by default, with 315+ additional custom brokers supported — the broadest coverage in the industry.
Real-World Results
“I’ve seen my spam emails decrease by about 50%, and spam phone calls have significantly reduced as well. Other employees have noticed this impact too, along with far fewer phishing attempts. We know the product is working, and it’s hard to believe how much of an impact it has had. If we tried to do these removals manually, it would never get done.”
— CISO, Multi-Billion-Dollar Regional Bank
Outcome:
Reduced phishing and smishing attempts, improved executive protection, minimized social engineering risk for long-term staff.

Enterprise-Ready
Platform
- SOC 2 Type II Attestation
- Admin Dashboard
- SAML, SCIM, SSO Integration
- Tiered Pricing for Role-Based Protection
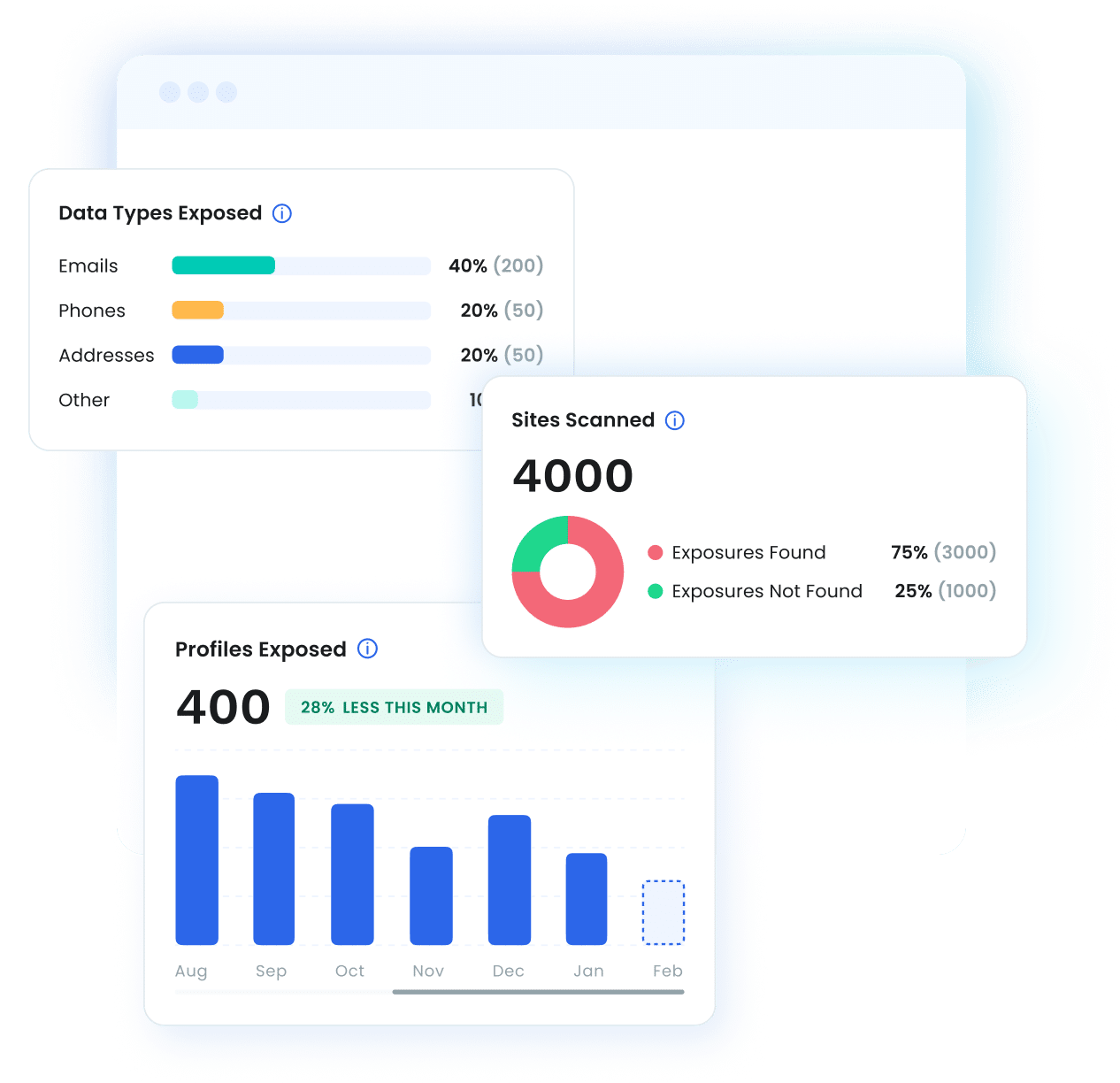
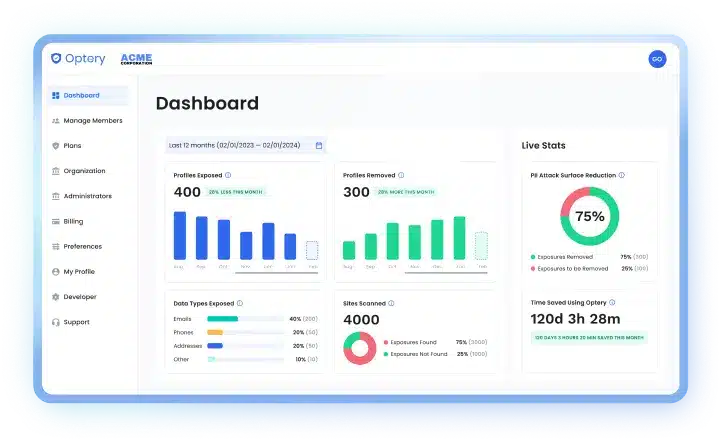
Track Impact.
Prove Value.
Organizations measure ROI through Optery’s business dashboard, which provides real-time metrics including:
- Profiles Removed vs. Exposed
- Types of PII Exposed
- Sites Scanned
- PII Attack Surface Reduction
- Time Saved: Automated vs. Manual Removals
These insights help teams track security gains, operational efficiency, and risk reduction over time.
See Optery in Action

Ready to increase your security posture?
Let’s connect.
Complete the form and an Optery team member will be in touch shortly.








