Welcome to The Optery Dispatch — a newsletter delivering the latest insights on threat intelligence and proactive cybersecurity strategy. In Issue #7, published November 25, 2025, we cover:
- Microsoft’s new Digital Defense Report shows ClickFix as the leading initial-access technique, underscoring how social engineering continues to outpace traditional defenses.
- A new phishing platform called Quantum Route Redirect automates credential theft campaigns and evades multiple layers of email security.
- DoorDash discloses a breach resulting from social engineering that exposed contact information of some of its customers, Dashers, and merchants.
Microsoft’s Digital Defense Report 2025 shows social engineering techniques dominating initial access methods, accounting for 89% of observed attacks
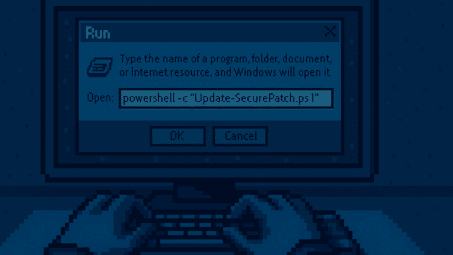
ClickFix has become a go-to initial access method which traditional phishing protections don’t catch
According to Microsoft’s new Digital Defense Report 2025, ClickFix topped the list of initial access methods observed by Microsoft Defender Experts over the past year. ClickFix is a social engineering technique that deceives users into copying and running malicious commands, disguised as “fixes,” CAPTCHA checks, or IT support prompts, directly in Windows Run, Terminal, or PowerShell.
With just a few keystrokes, attackers can deliver infostealers, remote-access Trojans, or worms, enabling credential theft and persistent access. ClickFix attacks are delivered via phishing, malvertising, and drive-by compromises, most of which impersonate legitimate brands and organizations. The report notes that traditional phishing protections won’t catch ClickFix.
To defend against ClickFix, Microsoft recommends implementing the following:
- “Teach users that pasting commands from unknown sources is as risky as clicking suspicious links.”
- “Enable PowerShell logging and use Constrained Language Mode to limit abuse.”
- “Watch for unusual clipboard activity followed by shell launches (cmd.exe, powershell.exe).”
- “Disable clipboard access and scripting in untrusted zones.”
- “Correlate clipboard usage with downstream execution patterns to catch suspicious flows.”
Of confirmed incidents escalated to Microsoft Defender Experts, where the initial access vector could be definitively determined, ClickFix accounted for 47% of intrusions, phishing for 35%, password spray for 10%, and drive-by compromise/SEO poisoning for 7%.
Adding together the methods of ClickFix, traditional phishing, and drive-by compromise/SEO poisoning, social engineering drove 89% of all attacks in Microsoft’s confirmed initial-access dataset.
Other findings
Across the broader threat landscape, the report highlights that malware families such as Lumma Stealer, RedLine, Vidar, Atomic Stealer, and Raccoon Stealer, once considered post-exploitation tools, are now being used as first-stage payloads. These infostealers are typically delivered through malvertising, SEO poisoning, cracked software, and social engineering techniques like ClickFix, and are designed to collect credentials, browser session tokens, and system context data at scale. Microsoft notes that these infections can escalate into enterprise-wide intrusions.
Microsoft additionally observed an uptick in device code phishing, where attackers abuse the device code authentication flow to obtain access and refresh tokens that can grant account access and support persistent or lateral movement as long as the token remains valid.
Email bombing, when an attacker floods a target’s inbox with hundreds or thousands of subscription emails, is described in the report as a particularly effective social-engineering tactic being used to obscure important alerts such as MFA prompts, password resets, fraud alerts, and transaction notifications, or to create confusion that attackers can exploit.
Across the report, Microsoft emphasizes “adversaries aren’t breaking in—they’re logging in.” MFA continues to be essential, though attackers are continuing to find new ways to circumvent it.
To reduce the number of social engineering attempts organizations must defend against, minimizing exposed employee PII wherever possible helps prevent attackers from being able to identify and target employees with their lures.
Read the full report for more insights: Microsoft Digital Defense Report 2025 | Microsoft
Quantum Route Redirect: A New Phishing Kit That Can Defeat Traditional Defenses
Powerful new phishing tool that can bypass multiple layers of security now targeting Microsoft 365 users
KnowBe4 researchers have identified a new phishing tool called “Quantum Route Redirect” (QRR), and it marks another step in the industrialization of social engineering.
The QRR kit comes with prebuilt phishing domains, brand-spoofing templates (DocuSign, payroll, payment notices, missed voicemail messages), and QR-code “quishing” support. Instead of attackers building their own infrastructure, QRR lets them launch large-scale credential-theft campaigns with minimal technical skill.
The platform’s biggest advantage is its automated traffic-routing engine. When the phishing link is activated, either by a security scanner or by an employee, QRR analyzes the request and determines whether it came from a bot or a real user.
Scanners are sent to harmless websites, making the email appear safe, while real users are redirected to convincing fake Microsoft 365 login pages designed to capture their credentials. This bot-vs-human filtering enables QRR to slip past Microsoft Exchange Online Protection, secure email gateways, integrated cloud email security tools, and even some web application firewalls.
KnowBe4 has identified roughly 1,000 domains hosting QRR, with victims in 90 countries; 76% of affected users are in the United States. The tool includes a dashboard with browser fingerprinting, VPN/proxy detection, analytics, and real-time statistics.
“Unfortunately, we believe the technology behind Quantum Route Redirect is here to stay and will likely increase in use as cybercriminals look to evade URL scanning technologies,” KnowBe4 noted.
As these turnkey kits spread, organizations should expect an increase in business-email–style lures, quishing attempts, and credential-harvesting campaigns.
Despite its sophistication, QRR still depends on one constant: attackers need personal information about employees to choose targets, shape believable lures, and increase success rates. Even the most advanced phishing kits can’t operate effectively without accurate contact details and job roles.
Minimizing that exposed PII remains one of the few steps organizations can take to meaningfully disrupt targeting before a phishing kit ever reaches an inbox.
Learn more: Quantum Route Redirect: Anonymous Tool Streamlining Global Phishing Attack
Microsoft 365 users targeted by major new phishing operation – here’s how to stay safe | TechRadar
DoorDash Breach Exposes Contact Information After Social Engineering Attack
Breach shows that basic contact details remain a valuable data type for attackers
DoorDash has confirmed a new data breach following a successful social engineering attack against an employee, allowing an unauthorized actor to access internal systems in late October.
According to the company, the attacker obtained contact information which may have included names, email addresses, phone numbers, and physical addresses belonging to customers, Dashers, and merchants. DoorDash emphasized that no SSNs, payment data, or passwords were accessed.
On November 12, DoorDash began notifying those affected. The notice states that ‘no sensitive data was accessed’. Commentators and security experts quickly took issue with the characterization of this data as ‘non-sensitive,’ as attackers rely on contact data for social engineering, impersonation, credential harvesting, account takeovers, and fraud. It is the same category of data that was undoubtedly needed to conduct the social engineering attack that breached DoorDash.
This breach is the latest in a series of security events for DoorDash. In 2019, the company reported a breach that exposed data belonging to roughly five million customers, Dashers, and merchants. Another breach followed in August 2022, linked to the same threat actors behind the 0ktapus campaign.
DoorDash users should be alert to unsolicited messages/phishing attempts that appear to come from DoorDash. Affected users should change their passwords and enable MFA, as attackers commonly pair exposed email addresses with breach-repository data to identify and crack credentials.
The compromise of personal devices via the exploitation of personal contact data can extend to work accounts when those devices are used for corporate access or MFA.
This breach is a reminder that contact information is sensitive, attackers treat it as valuable, and organizations must minimize its exposure in order to reduce their risk of breaches.
Read more: DoorDash hit by new data breach in October exposing user information
Thanks for reading! Want us to write about something specific? Submit a topic or idea.
If you’re looking to reduce your organization’s exposed PII and prevent phishing, voice and messaging scams, credential theft, and other PII-based threats, Optery can help. Get started here: Optery for business
Subscribe to receive future editions of The Optery Dispatch