Employee Privacy & Physical Security
- Remove Employee Personal Data.
- Reduce Cyber & Physical Risk.
- Protect Your People & Organization.

The Threat Landscape
Not all organizations face the same level of physical risk. For employees in public-facing, frontline, enforcement, or investigative roles, personal data exposure can translate directly into real-world harm.
Roles such as judges and court staff, law enforcement and border personnel, journalists, regulators, and other high-visibility or adversarial positions are more likely to be targeted for harassment, intimidation, stalking, or threats. In these environments, physical security risks often begin online.
Data broker sites openly publish and sell home addresses, phone numbers, family connections, employment details, and location information.

Threat actors and agitators and use exposed personal data on these sites to:use this data to:
- Locate home addresses
- Identify family members
- Target individuals for harassment, stalking, doxxing, or intimidation
- Enable swatting, threats, and physical confrontation
- Apply pressure to employees as leverage against an organization
Optery removes this exposed personal data more comprehensively than any other service, reducing the likelihood of real-world threats.
Protect Employees Beyond the Network
Reduce Physical Risk
Remove home addresses, phone numbers, and location data used to target employees.
Prevent Doxxing & Harassment
Eliminate the data used to publicly expose and intimidate individuals.
Disrupt Pre-Incident Reconnaissance
Remove personal data before it can be used to plan physical threats.
Protect High-Risk Roles
Safeguard employees whose work places them in public, adversarial, or enforcement-oriented positions.
Demonstrate Duty of Care
Show employees, leadership, and insurers that you are proactively reducing real-world risk.
Security, Risk & Compliance
Alignment
Optery supports duty-of-care and risk-management programs by addressing employee personal data exposure as a physical security concern:
NIST CSF 2.0: Supports Identify and Protect functions by reducing personal-data exposure that enables real-world targeting.
ISO 27001: Enhances risk management and personnel security controls by mitigating people-based threats.
Aligns with CIS Controls v8 by reducing people-based exposure that can contribute to security incidents.
SOC 2 Type II Attestation: Demonstrates that Optery securely processes, stores, and protects sensitive personal data.
Why Organizations
Choose Optery
Patented Search Technology
Finds significantly more exposed personal data per person — including addresses, phone numbers, and family links missed by competitors.
Before-and-After Screenshot Proof
The only service that provides visual evidence of personal data exposure reduction.
AI-Powered Automation
Automates complex opt-out workflows at scale with intelligence, autonomy, and precision — running securely on Optery’s private AWS Bedrock infrastructure. No personal data is shared with external model providers or used for training.
Unmatched Coverage
Covers 640+ brokers by default, with 315+ additional custom brokers supported — the broadest coverage in the industry.
Real-World Results
“We have some extremely sensitive clients, and I mean extremely sensitive clients, and we trust Optery to go out and clean up what’s out there as much as humanly possible.”
“Optery makes a huge difference in improving the security and reducing the risk of our clients. I don’t like hunting people online who have used Optery. I have clients who have used DeleteMe, and I don’t have to do much to find them. It’s extremely easy to find people who have used DeleteMe. With Optery, it’s different. I’m looking harder. It’s not particularly easy to do. There’s quality there. Post-Optery, it is definitely harder to hunt and target someone.”
— CEO, Executive Protection Firm
Outcome:
Reduced phishing and smishing attempts, improved executive protection, minimized social engineering risk for long-term staff.

Enterprise-Ready
Platform
- SOC 2 Type II Attestation
- Admin Dashboard
- SAML, SCIM, SSO Integration
- Tiered Pricing for Role-Based Protection
Track Impact.
Prove Value.
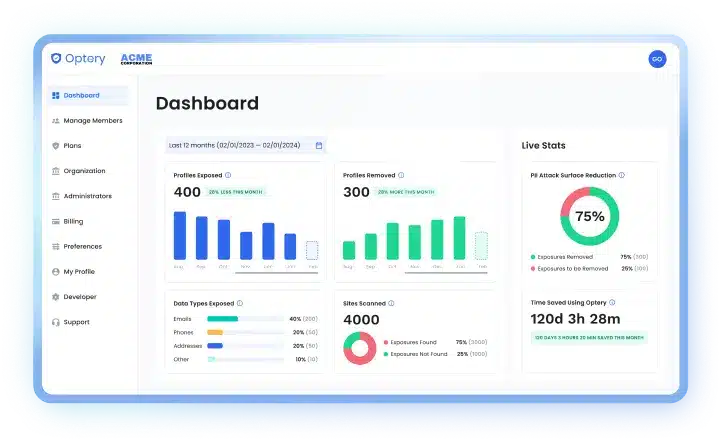
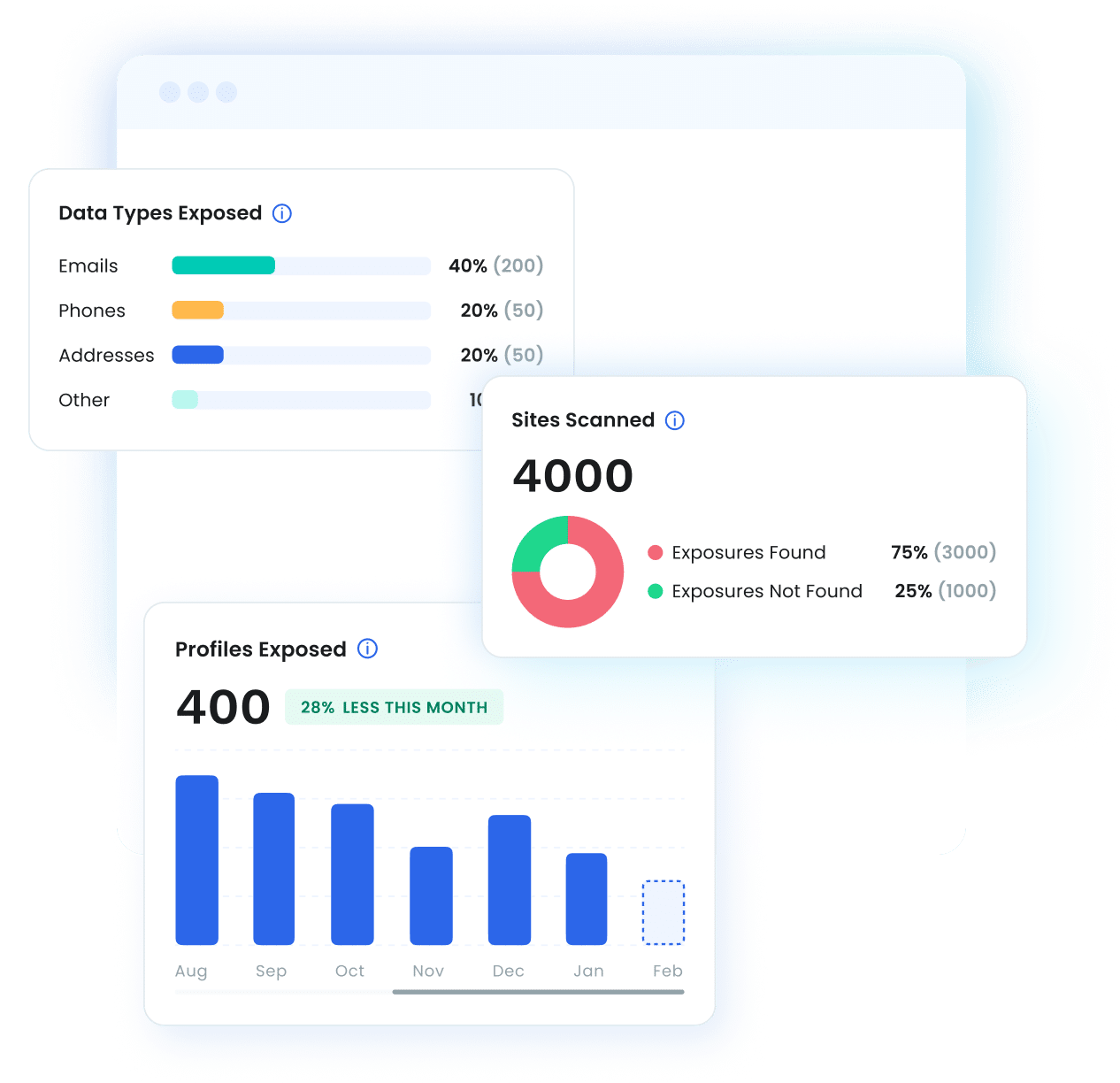
Organizations measure ROI through Optery’s business dashboard, which provides real-time metrics including:
- Profiles Removed vs. Exposed
- Types of PII Exposed
- Sites Scanned
- PII Attack Surface Reduction
- Time Saved: Automated vs. Manual Removals
These insights help teams track security gains, operational efficiency, and risk reduction over time.
See Optery in Action

Ready to increase your security posture?
Let’s connect.
Complete the form and an Optery team member will be in touch shortly.








