Insider Threat Prevention
- Remove Employee Personal Data.
- Reduce Cyber Risk.
- Protect Your Organization.

The Threat Landscape
Insider threats are not limited to malicious employees. Many incidents involve well-intentioned staff who are manipulated, coerced, or deceived by external threat actors. In other cases, attackers impersonate trusted employees or internal roles, using exposed personal details to bypass suspicion and gain cooperation.
Exposed personal data from data broker and people search sites enables attackers to socially engineer employees using private details to build trust, fabricate convincing scenarios, or extract sensitive information.
In more severe cases, exposed personal information can be leveraged for blackmail or coercion, pressuring employees to provide access to restricted systems or assist in an attack. By removing this data, organizations reduce the leverage attackers use to turn trusted insiders into unintentional accomplices.
Prevent Insider Threat Scenarios
Prevent Social Engineering of Trusted Employees
Remove the personal data attackers use to build credibility and manipulate insiders.
Limit Coercion & Blackmail Risk
Eliminate sensitive exposed personal details that can be used to pressure employees into unsafe actions.
Prevent Unauthorized Disclosure
Minimize the personal context attackers exploit to extract sensitive company information.
Protect Sensitive Roles & Long-Tenured Staff
Reduce risk of targeting or impersonation of employees with trusted access and institutional knowledge.
Complement Insider Risk Programs
Strengthen insider threat, IAM, and awareness efforts by removing external leverage.
Demonstrate Proactive Risk Reduction
Show leadership and auditors that you are addressing a critical insider threat vector.
Security, Risk & Compliance
Alignment
Optery supports insider threat risk reduction by addressing exposed personal data that enables manipulation and abuse of trust:
NIST CSF 2.0: Supports Identify and Protect functions by reducing external personal-data exposure used in insider threat scenarios
ISO 27001: Enhances risk management and threat mitigation related to human-centric attack vectors.
CIS Controls v8: Supports Controls 5 (Account Management) and 14 (Security Awareness) by reducing exploitable employee data.
SOC 2 Type II Attestation: Demonstrates that Optery securely processes, stores, and protects sensitive personal data.
Why Organizations Choose Optery
Patented Search Technology
Finds significantly more data broker profiles per person — ~100 on average, including 40–50 missed by competitors.
Before-and-After Screenshot Proof
The only service that provides before-and-after visual evidence of its effectiveness.
AI-Powered Automation
Automates complex opt-out workflows at scale with intelligence, autonomy, and precision — running securely on Optery’s private AWS Bedrock infrastructure. No personal data is shared with external model providers or used for training.
Unmatched Coverage
Covers 640+ brokers by default, with 315+ additional custom brokers supported — the broadest coverage in the industry.
Real-World Results
“We were particularly interested in protecting our long-term employees who have had the same email for many years and also our senior executives who have exposure through press releases and other public channels.”
“Our mobile phone numbers are a big part of our digital identity, and our CEO’s number has been spoofed many times. Optery has helped slow these impersonation attacks on our employees.”
“We know the product is working, and it’s hard to believe how much of an impact it has had.”
— CISO, Regional Bank
Outcome:
Reduced phishing and smishing attempts, improved executive protection, minimized social engineering risk for long-term staff.

Enterprise-Ready
Platform
- SOC 2 Type II Attestation
- Admin Dashboard
- SAML, SCIM, SSO Integration
- Tiered Pricing for Role-Based Protection
Track Impact.
Prove Value.
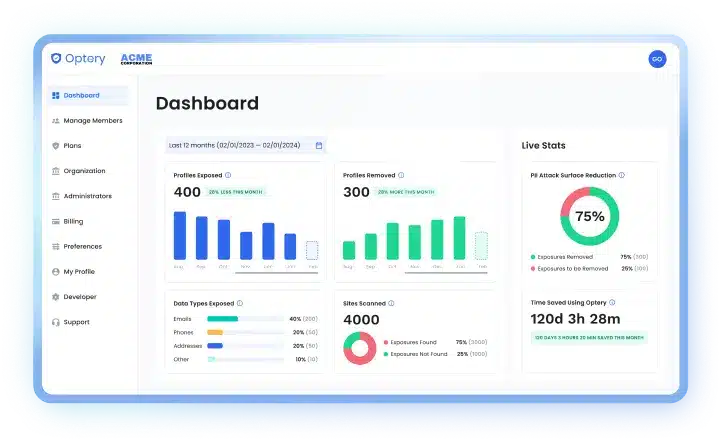
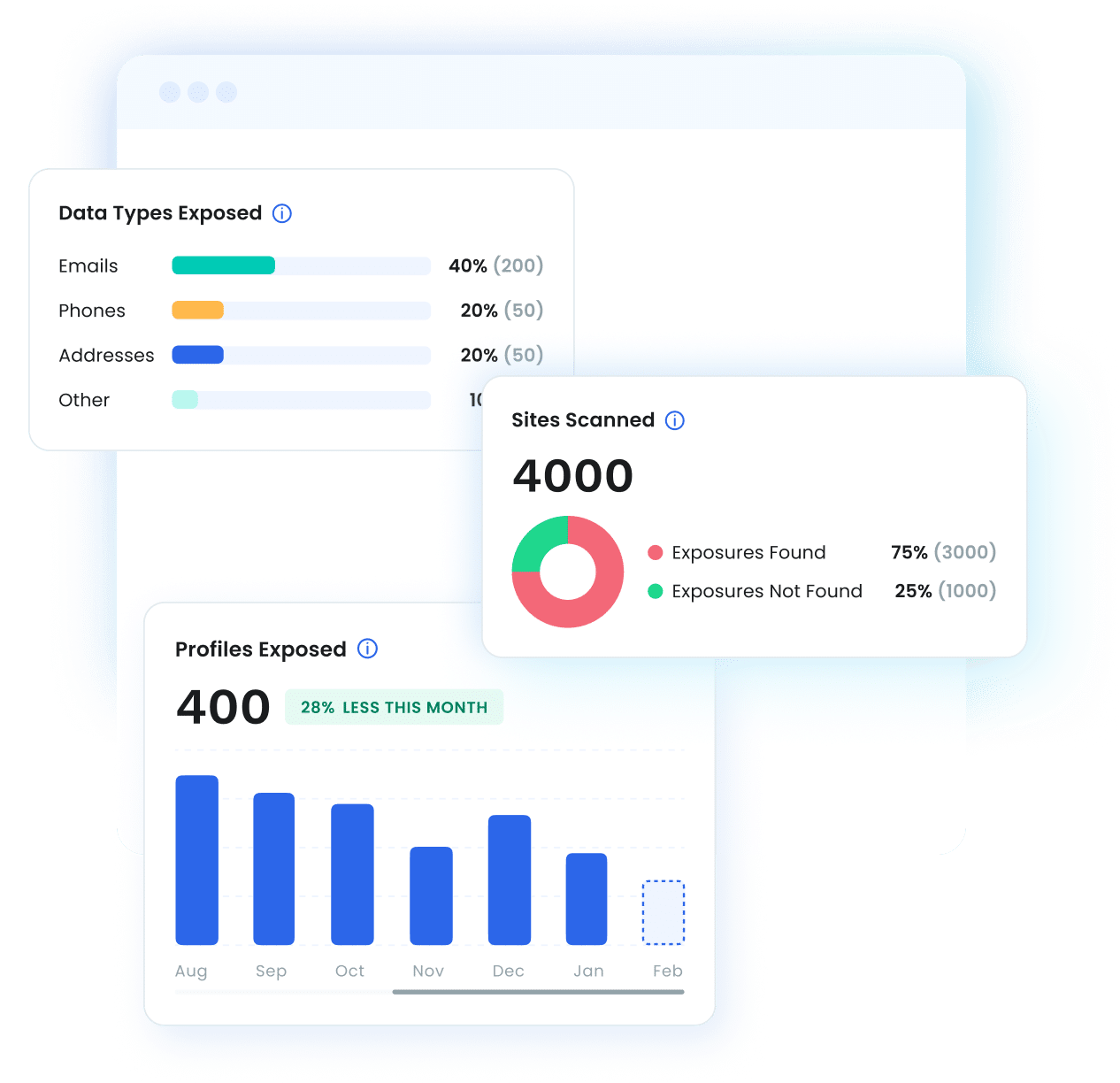
Organizations measure ROI through Optery’s business dashboard, which provides real-time metrics including:
- Profiles Removed vs. Exposed
- Types of PII Exposed
- Sites Scanned
- PII Attack Surface Reduction
- Time Saved: Automated vs. Manual Removals
These insights help teams track security gains, operational efficiency, and risk reduction over time.
See Optery in Action

Ready to increase your security posture?
Let’s connect.
Complete the form and an Optery team member will be in touch shortly.








