Cyber Attack Prevention
- Remove Employee Personal Data.
- Reduce Cyber Risk.
- Protect Your Organization.

The Threat Landscape
Most cyberattacks begin with reconnaissance, long before malware is deployed or alerts are triggered. According to the MITRE ATT&CK framework, adversaries conduct pre-attack intelligence gathering to understand their targets, including organizational structure and employee information.
Multiple threat actors have been documented using data broker sites as part of their reconnaissance process.

Threat actors use this data to:
- Identify employees, roles, and reporting structures
- Select high-value targets such as IT staff, executives, and long-tenured employees
- Combine exposed PII with leaked credentials to take over accounts
- Launch business email compromise, executive impersonation, and targeted fraud
- Tailor phishing, smishing, vishing, credential harvesting, and ransomware attacks
Optery removes this exposed personal data more comprehensively than any other service, disrupting a critical pre-attack phase of cyber operations.
This form of defensive cyber counterintelligence limits the information available to adversaries, making attacks harder to execute and prompting attackers to move on to easier targets.
Prevent Cyber Attacks Before They Start
Disrupt Attacker Reconnaissance
Remove the personal data adversaries use to plan and target attacks.
Reduce Phishing & Social Engineering Risk
Eliminate exposed PII used to craft convincing lures.
Thwart Credential-Based Attacks
Remove the data attackers use to find, crack, or harvest passwords.
Complement Detection & Response
Reduce the volume of targeted attacks that reach EDR, SIEM, and SOC workflows.
Demonstrate Proactive Risk Reduction
Show leadership and insurers that you are preventing attacks upstream.
Security, Risk & Compliance
Alignment
Optery supports cyber risk reduction by addressing exposed personal data as part of the external threat landscape:
NIST CSF 2.0: Supports Identify and Protect functions by reducing external personal-data exposure used in adversary reconnaissance.
ISO 27001: Enhances risk management and threat mitigation by addressing people-based attack vectors.
CIS Controls v8: Supports Controls 14 (Security Awareness) and 5 (Account Management) by reducing exploitable employee data.
SOC 2 Type II Attestation: Demonstrates that Optery securely processes, stores, and protects sensitive personal data.
Why Organizations
Choose Optery
Patented Search Technology
Finds significantly more data broker profiles per person — ~100 on average, including 40–50 missed by competitors.
Before-and-After Screenshot Proof
The only service that provides before-and-after visual evidence of its effectiveness.
AI-Powered Automation
Automates complex opt-out workflows at scale with intelligence, autonomy, and precision — running securely on Optery’s private AWS Bedrock infrastructure. No personal data is shared with external model providers or used for training.
Unmatched Coverage
Covers 635+ brokers by default, with 315+ additional custom brokers supported — the broadest coverage in the industry.
Real-World Results
“When I’m trying to find someone, as any OSINT course will tell you, the first place you’re going to go to is a data broker site and try to expand the profile of the person you are trying to get information on.”
“There’s so many things you can do with the data that’s out there on someone. If I have a name, an email, a location, I’m gonna then go see what data has been breached in connection with this info, then I’m going to be able to break into their accounts and target them in a variety of ways.”
“We have some extremely sensitive clients, and I mean extremely sensitive clients, and we trust Optery to go out and clean up what’s out there as much as humanly possible.”
“Post-Optery, it is definitely harder to hunt and target someone.”
— CEO, Executive Protection Firm
Outcome:
Reduced phishing and smishing attempts, improved executive protection, minimized social engineering risk for long-term staff.

Enterprise-Ready
Platform
- SOC 2 Type II Attestation
- Admin Dashboard
- SAML, SCIM, SSO Integration
- Tiered Pricing for Role-Based Protection
Track Impact.
Prove Value.
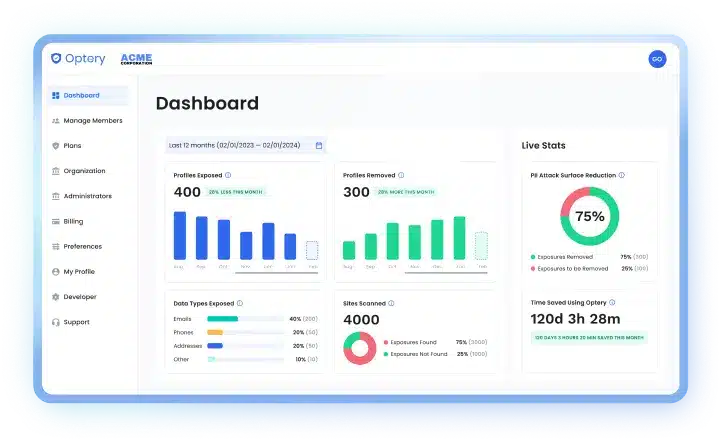
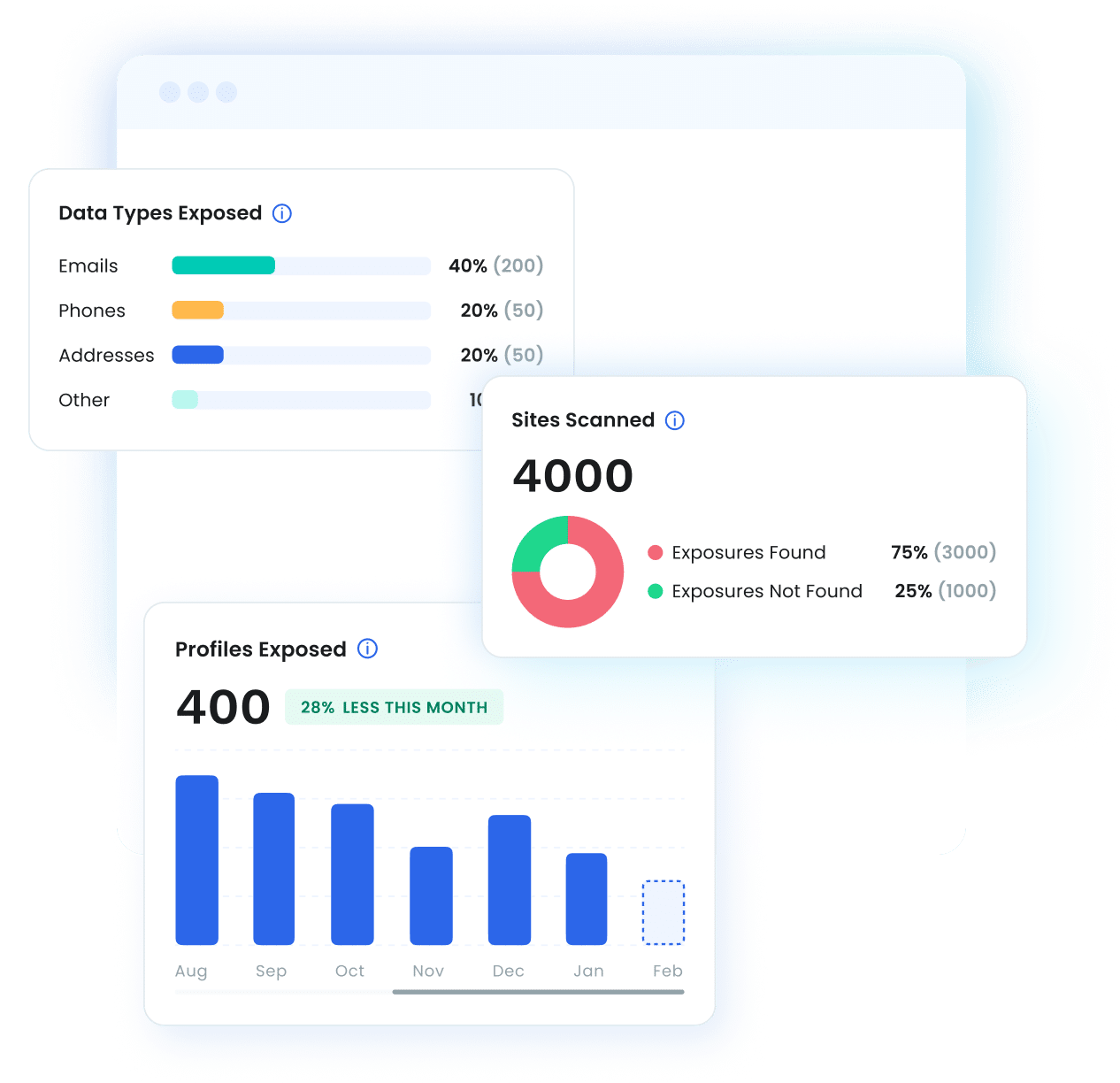
Organizations measure ROI through Optery’s business dashboard, which provides real-time metrics including:
- Profiles Removed vs. Exposed
- Types of PII Exposed
- Sites Scanned
- PII Attack Surface Reduction
- Time Saved: Automated vs. Manual Removals
These insights help teams track security gains, operational efficiency, and risk reduction over time.
See Optery in Action

Ready to increase your security posture?
Let’s connect.
Complete the form and an Optery team member will be in touch shortly.








