Attack Surface Management
- Remove Employee Personal Data.
- Reduce Cyber Risk.
- Protect Your Organization.

The Threat Landscape
Attack surface management has traditionally focused on internet-facing infrastructure, but today’s attackers most often exploit exposed employee data as an entry point. This data is used for social engineering and credential harvesting, which remain the leading drivers of compromise.
Exposed personal data is readily available on data broker sites, and multiple threat actors have been documented using these sites for reconnaissance and targeting.

Threat actors use data broker sites to:
- Map employee identities, roles, and reporting structures
- Identify high-value targets such as executives, IT staff, and long-tenured employees
- Fuel phishing, smishing, vishing, credential harvesting, and account takeover campaigns
Optery removes this exposed personal data more comprehensively than any other service, closing a critical gap in traditional attack surface management programs.
Strengthen Attack Surface Management
Reduce the Human Attack Surface
Remove exposed employee and executive PII that attackers exploit.
Disrupt Pre-Attack Reconnaissance
Eliminate the data attackers use to identify targets and plan attacks.
Complement External ASM Tools
Extend attack surface management beyond infrastructure to include people-based exposure.
Lower Incident Volume
Reduce the number of targeted attacks by shrinking the data attackers rely on.
Demonstrate Measurable Risk Reduction
Show leadership, auditors, and insurers that you are addressing a major, often overlooked attack surface.
Security, Risk & Compliance
Alignment
Optery strengthens core security and risk frameworks by addressing exposed personal data as part of the external attack surface:
NIST CSF 2.0: Supports Identify, Protect, and Detect functions by reducing external personal-data exposure that enables adversary reconnaissance and targeting.
ISO 27001: Enhances controls related to risk management, access control, identity security, and threat mitigation.
CIS Controls v8: Supports Controls 5 (Account Management), 14 (Security Awareness), and 15 (Service Provider Management) by reducing exploitable employee data used in attacks.
SOC 2 Type II Attestation: Demonstrates that Optery securely processes, stores, and protects sensitive personal data.
Why Organizations
Choose Optery
Patented Search Technology
Finds significantly more data broker profiles per person — ~100 on average, including 40–50 missed by competitors.
Before-and-After Screenshot Proof
The only service that provides before-and-after visual evidence of our effectiveness.
AI-Powered Automation
Automates complex opt-out workflows at scale with intelligence, autonomy, and precision — running securely on Optery’s private AWS Bedrock infrastructure. No personal data is shared with external model providers or used for training.
Unmatched Coverage
Covers 635+ brokers by default, with 715+ additional custom brokers supported — the broadest coverage in the industry.
Real-World Results
“Bad actors were regularly targeting my employees with spear-phishing campaigns via text messages. The level of effort and sophistication that the bad guys employ in their reconnaissance and impersonation campaigns is impressive. I knew I needed to minimize my team’s exposure if I wanted to reduce the risk to my employees and my company.”
“The need for Optery’s service is very high, and I had been waiting for a company like this for years.”
“Optery protects my company by protecting my people from being targeted. When you minimize your visibility, threat actors will move on to other companies.”
— CEO, Healthcare Analytics Company
Outcome:
Reduced phishing and smishing attempts, improved executive protection, minimized social engineering risk for long-term staff.

Enterprise-Ready
Platform
- SOC 2 Type II Attestation
- Admin Dashboard
- SAML, SCIM, SSO Integration
- Tiered Pricing for Role-Based Protection
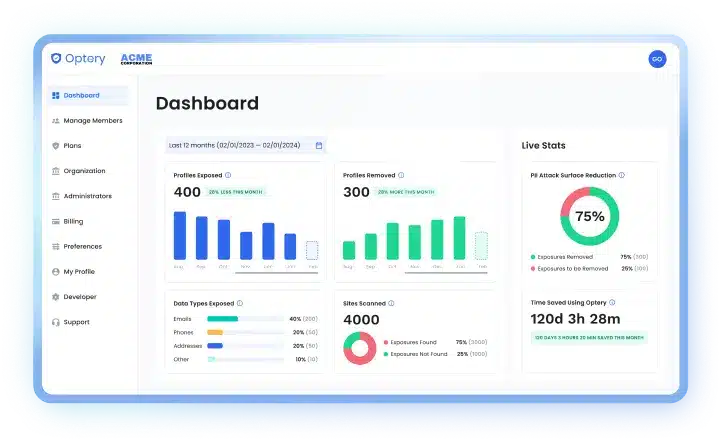
Track Impact.
Prove Value.
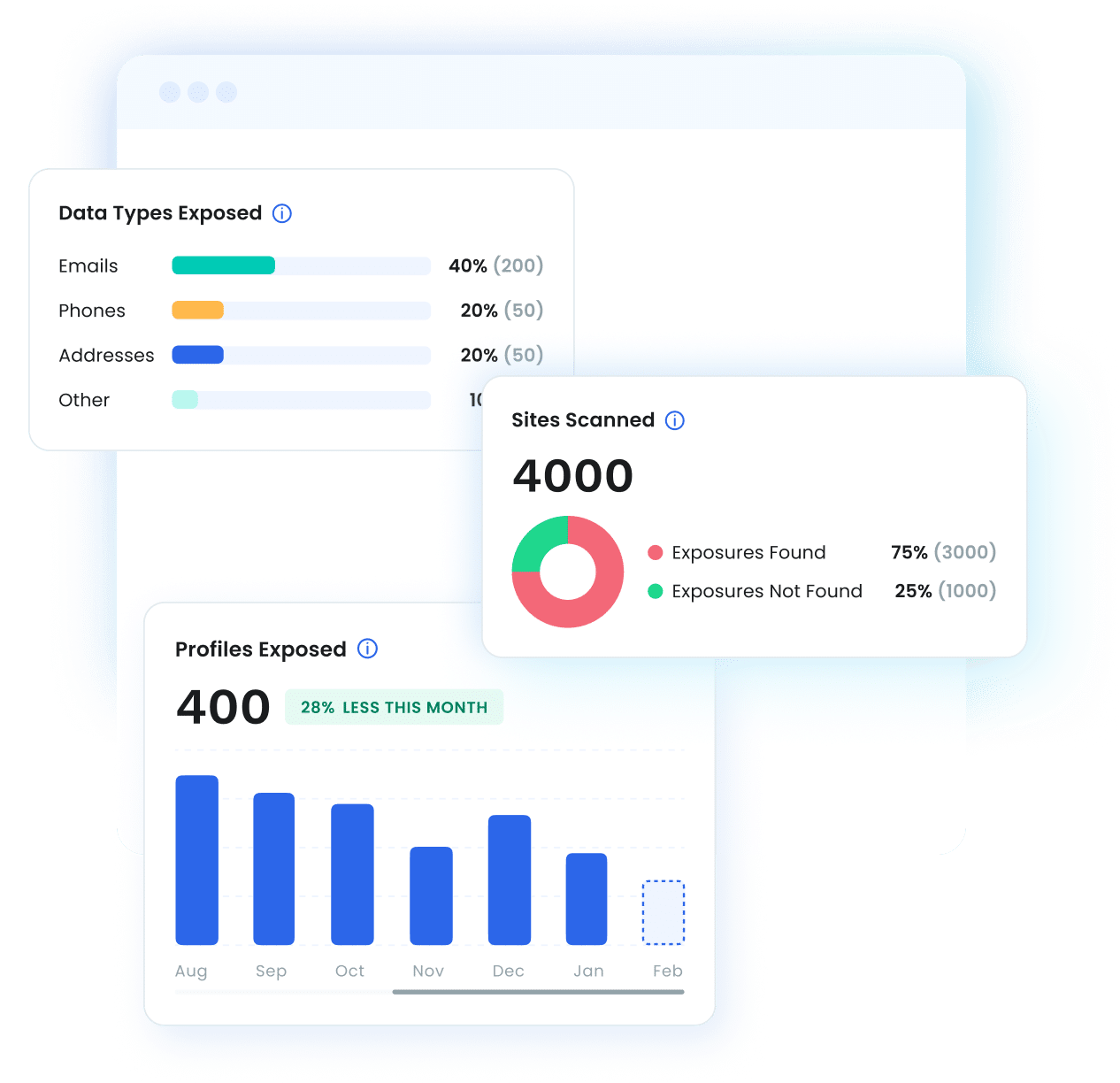
Organizations measure ROI through Optery’s business dashboard, which provides real-time metrics including:
- Profiles Removed vs. Exposed
- Types of PII Exposed
- Sites Scanned
- PII Attack Surface Reduction
- Time Saved: Automated vs. Manual Removals
These insights help teams track security gains, operational efficiency, and risk reduction over time.
See Optery in Action

Ready to increase your security posture?
Let’s connect.
Complete the form and an Optery team member will be in touch shortly.







